Upgrading to macOS 26 and the Post-Quantum Era
I’ve always enjoyed the feeling of upgrading my PC’s operating system — that sense of a fresh start, cleaner design, and new capabilities under the hood.
With macOS 26, Apple has introduced the visually delightful (but functionally questionable) Liquid Glassinterface.
But beyond the aesthetics, a feature I was interested to test was Safari’s new support for Post-Quantum Cryptography (PQC). Previously, when using macOS 18, pq.cloudflareresearch.com would show me a red status. But now, it states that my browser is using X25519MLKEM768 alongside a green status.
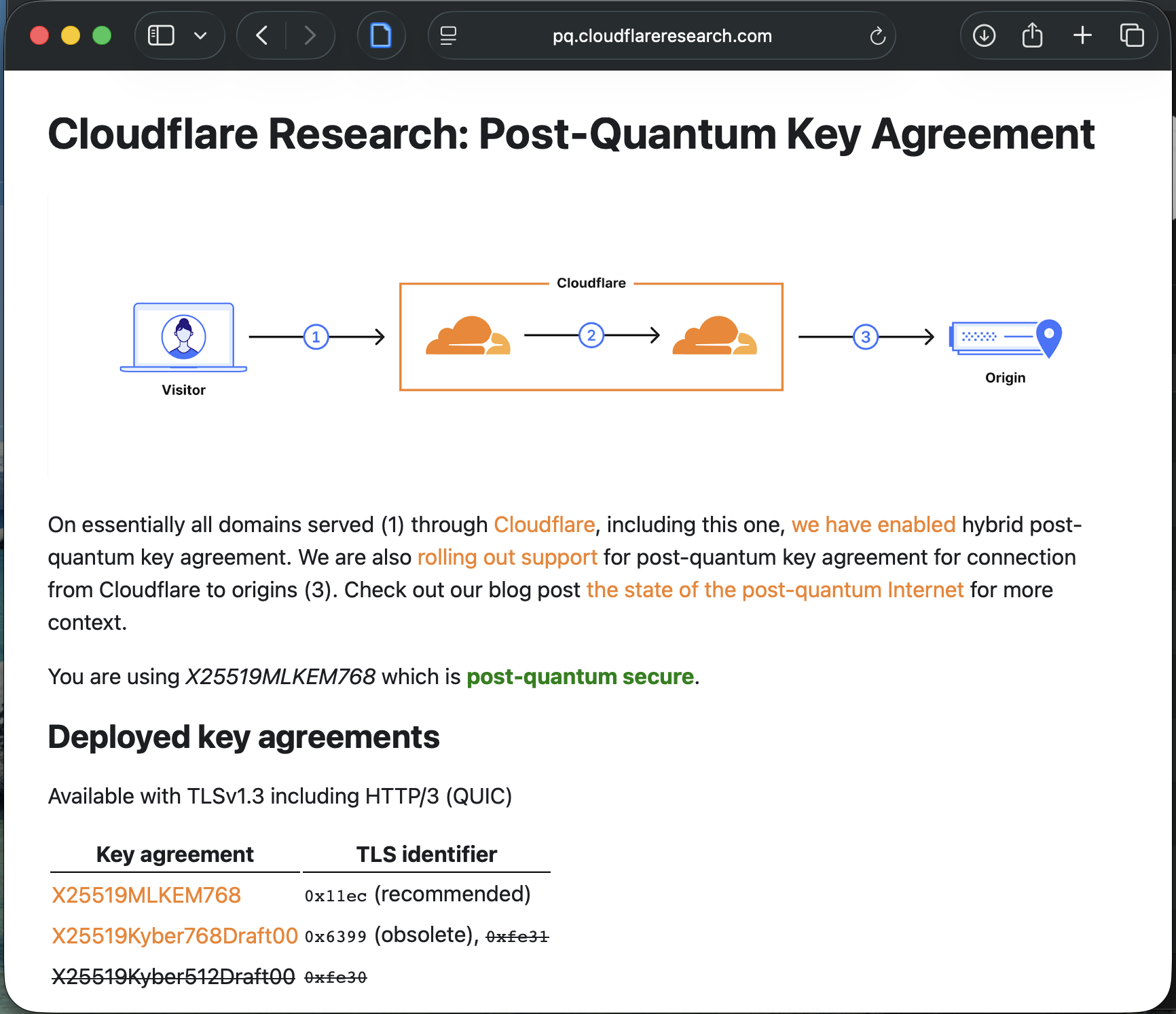
2025 is officially the International Year of Quantum Science and Technology, and fittingly, it’s also the year many major software platforms are beginning to enable post-quantum encryption by default. Besides browsers adopting PQC for TLS and QUIC connections, openSSH library has also switched over to a hybrid key-exchange algorithm by default since version 9.8.
GitHub recently announced that ssh to their services is now post-quantum safe but only for github.com and non-US resident GitHub Enterprise Cloud regions. Why non-US? Because their only sshd hybrid key exchange algo sntrup761x25519-sha512 is not FIPS compliant. My guess is that github upgraded their openSSH installation to v9.8 only because in v9.9, openSSH has the mlkem768x25519-sha256 algo which is FIPS compliant.
It’s worth noting, however, that only the key-exchange phase of SSH is has been upgraded with PQC. The SSH keys you generate with commands such as ssh-keygen -t rsa for authentication are still classical keys. Though still vulnerable to quantum computers, those keys are protected by the symmetrically encrypted channel established by the quantum-resistant key exchange mechanism.
